Our Cybersecurity Services


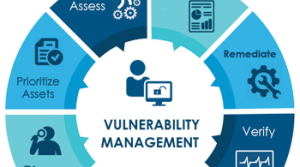
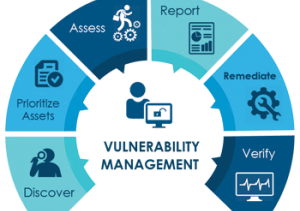
Vulnerability Assessmentand Management:
Vulnerability assessment and management is a crucial process that involves identifying and mitigating vulnerabilities in various technologies. It encompasses the evaluation of operating systems, networks, mobile applications, web applications, and other technologies to identify weaknesses that could be exploited by malicious actors. By conducting regular vulnerability assessments, organizations can proactively identify potential risks and take appropriate measures to prevent security breaches. This includes implementing necessary patches, updates, and security controls to minimize the impact of vulnerabilities. Additionally, vulnerability management involves monitoring and tracking vulnerabilities over time to ensure continuous protection. It is an essential component of a comprehensive cybersecurity strategy, as it helps organizations stay ahead of potential threats and safeguard their critical assets and sensitive information.
Penetration Testing:
Penetration testing, also known as ethical hacking, is a valuable service offered to customers to enhance their cybersecurity. It involves simulating real-world attacks on a network, system, or application to identify vulnerabilities and weaknesses. By conducting penetration testing, businesses can proactively identify potential entry points for malicious hackers and take appropriate measures to strengthen their defenses. This service provides customers with a comprehensive understanding of their security posture, allowing them to address any vulnerabilities before they are exploited by cybercriminals. Penetration testing helps organizations meet compliance requirements, safeguard sensitive data, and protect their reputation. With the ever-increasing sophistication of cyber threats, this service is essential in ensuring the security and resilience of customer systems and networks.


Red Teaming:
Red teaming is a strategic approach aimed at enhancing the security and resilience of an organization. It involves simulating realistic attack scenarios to identify vulnerabilities and weaknesses in the existing systems, processes, and procedures. By adopting the perspective of an adversary, red teamers can provide valuable insights into the effectiveness of an organization's security measures. Through careful analysis and evaluation, they can uncover hidden risks and potential avenues of exploitation that might otherwise go unnoticed. Red teaming helps organizations to proactively identify and address security gaps, enabling them to strengthen their defenses and mitigate potential threats. By engaging in this practice, businesses can better understand their vulnerabilities and develop robust strategies to protect themselves against the ever-evolving landscape of cyber threats.
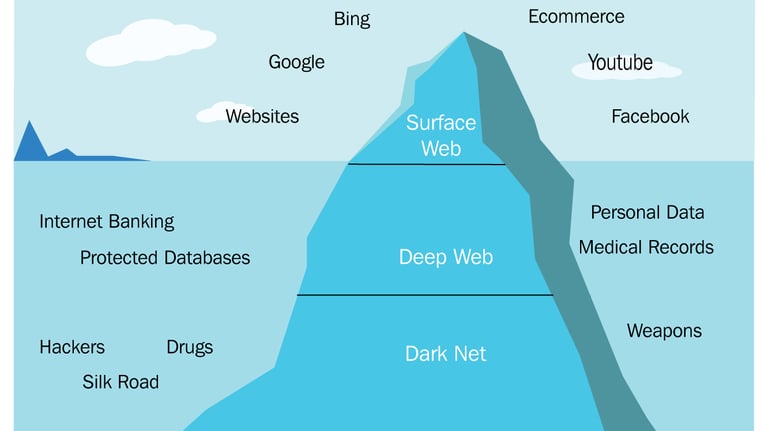
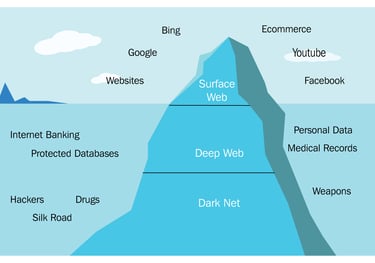
Dark Web Analysis:
Our company specializes in providing comprehensive Dark Web analysis services to our clients. The Dark Web is a hidden part of the internet that cannot be accessed through traditional search engines, making it a breeding ground for illegal activities. With our expertise and advanced tools, we conduct thorough investigations and gather valuable intelligence from the Dark Web to help our clients mitigate risks and protect their assets. We monitor various platforms and forums where criminal activities, such as hacking, drug trafficking, and identity theft, take place, allowing us to identify potential threats and vulnerabilities. Our team of skilled analysts is dedicated to staying abreast of the latest trends and techniques used by cybercriminals, enabling us to provide our clients with actionable insights and proactive security measures. By leveraging the power of Dark Web analysis, we empower our clients to stay one step ahead of cyber threats and safeguard their business interests.
End Point Protection:
End-point protection is an essential component of a company's cybersecurity strategy for safeguarding its clients. It focuses on protecting network endpoints, such as laptops, desktops, and mobile devices, from various cyber threats. By implementing robust security measures, such as antivirus software, firewalls, and encryption, End Point Protection ensures that client data remains secure and confidential. It prevents unauthorized access, malware attacks, and data breaches, thereby minimizing the risk of financial losses and reputational damage. Regular updates and patches are also crucial to keep the endpoints protected against emerging threats. With the increasing sophistication of cyber attacks, having a comprehensive end-point protection solution in place is vital for companies to maintain their clients' trust and confidence in their services.




Security Operations Center:
The company offers security operations center deployment and monitoring services to its prospective customers. With a dedicated team of experts, the company ensures the highest level of security for its clients' valuable assets. The security operations center is equipped with state-of-the-art technology and advanced monitoring tools to detect and respond to any potential threats or breaches in real-time. By continuously monitoring and analyzing network activities, the company can proactively identify vulnerabilities and take immediate actions to mitigate risks. The team of skilled professionals stays vigilant 24/7 to ensure the security posture of the customers' infrastructure. With a comprehensive and tailored approach, the company aims to provide a robust and reliable security solution that aligns with the customers' specific needs and requirements.
Information Systems Audit:
Information Systems Audit can provide several benefits to organizations. Firstly, it helps in identifying any potential risks or vulnerabilities in the organization's information systems. This allows the management to take appropriate measures to mitigate these risks and ensure the security of their data. Secondly, it helps in ensuring compliance with various regulatory requirements and industry standards. By conducting regular audits, organizations can demonstrate their adherence to these standards, which in turn enhances their reputation and credibility. Additionally, Information Systems Audit helps in improving the efficiency and effectiveness of the organization's IT processes. By identifying any inefficiencies or bottlenecks, organizations can streamline their operations and optimize their resources. Overall, Information Systems Audit plays a crucial role in safeguarding the organization's assets, maintaining compliance, and enhancing operational performance.
ISO 27001/ISMS:
Implementing ISO 27001 can bring several benefits to organizations. Firstly, it helps in safeguarding sensitive information and data by establishing robust security controls and risk management processes. This ensures the confidentiality, integrity, and availability of information assets. Secondly, ISO 27001 enhances the organization's reputation as it demonstrates their commitment to maintaining high standards of information security. This can be particularly valuable for organizations that handle sensitive customer data or operate in regulated industries. Thirdly, ISO 27001 provides a systematic approach to managing security risks, which helps in identifying and addressing vulnerabilities proactively. This results in reduced security incidents and potential financial losses. Additionally, ISO 27001 compliance can also open doors to new business opportunities, as it gives organizations a competitive edge by assuring customers and partners about their commitment to information security best practices. Overall, implementing ISO 27001 can strengthen an organization's security posture, improve its reputation, and enhance its business resilience.






Security Operations Center:
A Security Operations Center (SOC) offers several benefits to organizations in enhancing their overall security posture. Firstly, a SOC provides round-the-clock monitoring and threat detection capabilities, ensuring timely identification and response to security incidents. This proactive approach helps in mitigating potential risks and minimizing the impact of cyber-attacks. Additionally, SOC teams possess advanced tools and technologies, enabling them to conduct in-depth investigationsaand analysis of security events. This helps in better understanding the attack vectors and patterns, leading to improved incident response strategies. Moreover, a SOC enhances collaboration and information sharing across different teams within an organization, fostering a unified approach to security. By centralizing security operations, SOC also enables organizations to achieve compliance with industry regulations and standards. Overall, investing in a SOC empowers organizations to proactively protect their critical assets and sensitive information from evolving cyber threats.
Swift CSP:
Enhanced Cyber Defences: Swift CSP updates and fortifies financial institutions' cyber defenses.
Security Controls Framework: The CSCF establishes a security baseline for the organizations.
Annual Compliance Attestation: Organizations annually attest their compliance, reflecting a proactive organization.
Independent Assessment: Attestations are supported by independent assessments.
Risk Management: The program enhances counterparty risk management and protection for core payment systems.
Community Transparency: Compliance levels are shared through Security Attestations, increasing transparency.
Trust and Confidence: Compliance demonstration improves customer trust and confidence.
Counterparty Assessment: The program enables security posture assessment of counterparties and partners.
Adaptability: Swift CSP evolves with the changing cyber threat landscape.
Fraud Prevention: The program aids in detecting and preventing fraudulent activities.
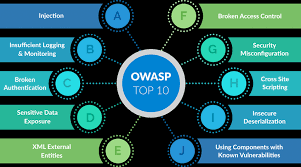
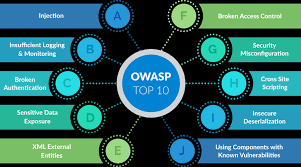
Web Site/Web Application Sec:
Enhanced Security: SATL's secure web development practices protect against cyber threats, ensuring the safety of user data.
Trust and Confidence: Secure websites foster trust among users, enhancing the company's reputation.
Data Protection: Robust security measures prevent data breaches, protecting sensitive information.
Compliance: SATL's secure web development adheres to industry standards, ensuring compliance with regulations.
Rapid Development: SATL's efficient development process ensures quick delivery without compromising on quality.
Professionalism: The professional approach of SATL guarantees a user-friendly interface and reliable functionality.
Cost-Effective: Secure development practices can reduce the cost of identifying and protecting apps from security vulnerabilities. Investor and Lender Trust: Secure web development can boost trust from investors and lenders.
A secure website or web application developed by SATL can provide a safe, efficient, and user-friendly platform that enhances customer trust and meets industry standards. This not only protects the customer's data but also contributes to the overall success of their business.




Digital Marketing and SEO:
360° SEO Audit: The company conducts a comprehensive audit of the client's SEO landscape.
Customized SEO Action Plan: The company develops a long-term SEO strategy based on the client's business goals.
Dedicated Marketing Team: Clients are assigned a dedicated team for their marketing needs.
Industry-Specific Expertise: The company provides experts who have specific knowledge of the client's industry.
Access to Marketing Tools: Clients are given access to the company's marketing software and tools.
Transparent Reporting: The company maintains regular communication and provides transparent reporting to its clients.
Local SEO Services: The company optimizes the client's website and local listings for local searches.
E-commerce SEO Services: The company optimizes the client's website for online shopping.
Voice SEO Services: The company optimizes the client's website for voice searches.
SEO Audit Services: The company identifies and fixes the client's website’s biggest SEO issues.
Driving Revenue: The company aims to drive revenue for the client through professional digital marketing services.
Omni-Channel Digital Strategy: The company crafts a multi-channel digital strategy to help the client drive revenue from digital marketing.
AI-Powered Technology: The company uses AI-powered technology for data-backed campaigns.
Affordable SEO Plans: The company offers affordable monthly SEO plans.
Brand Building: The company helps build the client's brand through SEO.
Local SEO: The company provides services specifically tailored for local SEO.
CANADA
connect@mysatl.com
Local Office Hours:
Mon-Sun
07:00-17:00
USA
connect@mysatl.com
Local Office Hours:
Mon-Sun
07:00-17:00
GERMANY
connect@mysatl.com
Local Office Hours:
Mon-Sun
07:00-17:00
FINLAND
connect@mysatl.com
Local Office Hours:
Mon-Sun
07:00-17:00
QATAR
connect@mysatl.com
Local Office Hours:
Mon-Sun
07:00-17:00
BANGLADESH
connect@mysatl.com
Local Office Hours:
24/7/365
Cell: +88 01744 201 201
© Copyrights
@SATL. All rights reserved.


